Scanning Networks ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner
Scanning is an important phase and a hacker needs to have knowledge of operating systems, ports, protocols and networks.ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner
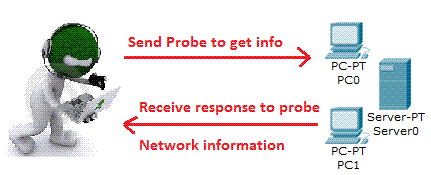
In this phase the target system is scanned to look for open ports and vulnerabilities. One can find reach ability of devices using the ping command and then run port scans on the active IPs. This phase is still a part of the information gathering but is more interesting than the footprinting phase and this begins to give you the feel of hacking.
It is in this phase that we get to know:
- Live systems on the network by pinging
- Find out services that are run on target
- Find the TCP and UDP ports and services
- Find the Operating System running on the target
Types of Scanning
- Port Scanning : To find open ports and services on target
- Network Scanning: Find IP address in the network of the target
- Vulnerability Scanning: Find weakness or vulnerabilities on the target
ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner
Port Scanning: In this process the hacker identifies available and open ports and understands what services are running. You must understand the ports and port numbers. The ports numbers can be in these three ranges:
- Well known Ports from 0 to 1023
- Registered ports from 1024 to 49151
- Dynamic Ports from 49152 to 65535
ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner
In you are using a Windows system, you can see the common or well-known ports in the below path: C:\Windows\System32\Drivers\etc\services
Some common port numbers are as below:
| Port Number | Service |
Network Scanning: This means to look for active machines or targets on the network. This can be done using tools or scripts that ping to all IP addresses on the networks and get a list of the alive nodes and their IP addresses.
Vulnerability Scanning: This is the mechanism where the target is scanned or looked for any vulnerability. In this scan the Operating system is found out with installed patches etc and then based on the information vulnerabilities are found in that particular version of Operating System.
ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner
If you use scanning on a target network, if the target network has Intrusion Detection System (IDS) installed, then the hacker or scanner can be traced back easily. The IDS then send alert on the system that someone is trying to seek information from the system. Being a CEH if you perform any scans it should not be detected, as we would not want target systems to know someone is trying to attack their system.
Scanning Methodology
This is the sequence or steps how the scanning needs to be carried out and what information needs to be collected and documented so it can be used for further phases of hacking.
Steps or phases for scanning
Look for Live Systems -> Check for Open Ports -> Identify running services -> Check running Operating System ( OS Footprinting) -> Scan Vulnerabilities -> Document details and draw Network diagram -> Prepare Proxies to avoid being caught -> Proceed with Attack
Looking for Live systems, this is done either using the normal PING command or using third party tools or scripts to run multiple pings to destination or target.
As we know PING uses the protocol ICMP, thus an ICMP echo request is sent to the destination or target IP address, if the target is active or alive it would respond with an ICMP Reply. This also informs if ICMP can be passed through a firewall. Mostly organizations have started blocking ICMP requests to be safe from attacks.
NMAP is a very popular tool used for scanning. It can be downloaded from the below link.
ip scanner
port scanner
ip scan
ceh course
hacking certification
network scanner windows
advanced network scanner







No comments:
Post a Comment